If a USB drive is **physically damaged** or **has corrupted firmware** to the extent that it is not recognizable or repairable by conventional methods, there's little that can be done through software to "fix" it. In many cases, hardware repair or professional data recovery services are required.
However, if the issue with the USB drive is related to **software corruption** (like file system errors, partition table corruption, or damaged data sectors), Python can be used to attempt a recovery or repair of the drive. Below are some potential steps you can follow to try to repair the USB drive programmatically.
### 1. **Check if the USB Drive is Accessible**
You can first check if the drive is detected by the system.
```python
import os
import sys
def list_drives():
if sys.platform == "win32":
# For Windows
drives = [d for d in "ABCDEFGHIJKLMNOPQRSTUVWXYZ" if os.path.exists(f"{d}:\\")]
return drives
else:
# For Linux/macOS, list drives via '/dev'
drives = [f"/dev/{device}" for device in os.listdir("/dev") if "sd" in device]
return drives
print("Detected Drives:")
print(list_drives())
```
If the USB drive is visible in the list of drives, you can proceed to try fixing it.
---
### 2. **Check the USB Drive's File System**
If the file system is corrupt (e.g., FAT32, NTFS, exFAT), you can attempt to repair it using Python by invoking system utilities.
For **Windows**, you can use the `chkdsk` command to repair the file system. You can invoke this from Python using the `subprocess` module:
#### Windows: Using `chkdsk` to Repair File System
```python
import subprocess
def repair_drive_windows(drive_letter):
try:
# Running chkdsk to repair the drive (replace 'X' with the correct drive letter)
subprocess.run(f"chkdsk {drive_letter}: /f", shell=True, check=True)
print(f"Drive {drive_letter}: repair completed.")
except subprocess.CalledProcessError as e:
print(f"Error during repair: {e}")
# Replace with the drive letter of the USB drive
repair_drive_windows("E")
```
#### Linux/macOS: Using `fsck` to Repair File System
On **Linux** or **macOS**, you can use `fsck` (File System Consistency Check) to attempt repairing the drive's file system.
```python
import subprocess
def repair_drive_linux(device_path):
try:
# Running fsck to repair the drive (replace '/dev/sdX' with the correct device path)
subprocess.run(f"sudo fsck {device_path}", shell=True, check=True)
print(f"Drive {device_path} repair completed.")
except subprocess.CalledProcessError as e:
print(f"Error during repair: {e}")
# Replace with the device path of the USB drive, e.g., "/dev/sdb1"
repair_drive_linux("/dev/sdb1")
```
Make sure that the drive is unmounted before you attempt running `fsck`. You can unmount it using the `umount` command in Linux/macOS.
---
### 3. **Attempt Data Recovery Using `pySMART` (SMART Data for Hard Drives)**
For USB drives that are failing but still accessible, you can attempt to gather some SMART (Self-Monitoring, Analysis, and Reporting Technology) data to see if the drive is physically deteriorating. Python has a library called **`pySMART`** that can be used to fetch SMART data.
You can install it via pip:
```bash
pip install pysmart
```
Example to check SMART status:
```python
from pysmart.smart import Smart
def check_smart_status(drive):
try:
smart = Smart(drive)
smart_data = smart.info()
print(f"SMART data for {drive}: {smart_data}")
except Exception as e:
print(f"Error retrieving SMART data for {drive}: {e}")
# Replace with the actual device, e.g., '/dev/sdb'
check_smart_status('/dev/sdb')
```
If the SMART data indicates **bad sectors** or **other hardware issues**, the USB drive might be physically damaged and cannot be repaired through software.
---
### 4. **Reformatting the Drive**
If the USB drive is still accessible and no important data needs recovery, you can attempt to reformat the drive using Python. This is a **destructive** action and will erase all data on the drive.
```python
import os
import subprocess
def format_usb_drive(drive_letter):
try:
# Windows: Format the drive (replace 'X' with the correct drive letter)
subprocess.run(f"format {drive_letter}: /fs:ntfs /q /x", shell=True, check=True)
print(f"Drive {drive_letter}: formatted successfully.")
except subprocess.CalledProcessError as e:
print(f"Error during format: {e}")
# Replace with the correct drive letter, e.g., 'E'
format_usb_drive("E")
```
For **Linux/macOS**, you can use the `mkfs` tool to format the drive:
```python
import subprocess
def format_usb_drive_linux(device_path):
try:
# Format the USB drive with ext4 or any other file system
subprocess.run(f"sudo mkfs.ext4 {device_path}", shell=True, check=True)
print(f"Drive {device_path}: formatted successfully.")
except subprocess.CalledProcessError as e:
print(f"Error during format: {e}")
# Replace with the correct device path, e.g., '/dev/sdb1'
format_usb_drive_linux("/dev/sdb1")
```
---
### 5. **Data Recovery from a Damaged USB Drive**
If the USB drive has logical corruption but is still physically working, you can attempt to recover data using Python libraries like `pytsk3` (The Sleuth Kit) or `photorescue` (for photos and videos), though these are advanced and require in-depth knowledge of forensic data recovery.
Here is an example of using **`pytsk3`** to examine the file system and recover files:
```bash
pip install pytsk3
```
```python
import pytsk3
import sys
def recover_files(drive_path):
try:
img = pytsk3.Img_Info(drive_path)
fs = pytsk3.FS_Info(img)
# List files in the root directory
directory = fs.open_dir(path="/")
for entry in directory:
if entry.info.name:
print(f"Found file: {entry.info.name}")
# Further recovery logic would go here...
except Exception as e:
print(f"Error during file recovery: {e}")
# Replace with the correct device path, e.g., '/dev/sdb1'
recover_files("/dev/sdb1")
```
---
### Conclusion
If your USB drive is **physically damaged** or has **hardware failure**, software alone won't be able to fix it. You would need to either repair the hardware (which is often not feasible without professional assistance) or use **data recovery services** to recover important data from the damaged drive.
If the problem is **software corruption** (e.g., file system errors), the methods above might help you repair or recover the drive.
Remember, any attempt to fix a failing USB drive carries the risk of **data loss**, so if the data is important, consider using professional data recovery services before proceeding with formatting or other destructive actions.
Awesome Basic Tips and Tricks
Thursday, November 21, 2024
Repair USB Drive
Saturday, April 7, 2012
100+ Run Commands
- Accessibility Options : access.cpl
- Add Hardware: hdwwiz.cpl
- Add / Remove Programs: appwiz.cpl
- Administrative Tools : control admintools
- Automatic Updates: wuaucpl.cpl
- Wizard file transfer Bluethooth: fsquirt
- Calculator: calc
- Certificate Manager: certmgr.msc
- Character: charmap
- Checking disk : chkdsk
- Manager of the album (clipboard) : clipbrd
- Command Prompt : cmd
- Service components (DCOM) : dcomcnfg
- Computer Management : compmgmt.msc
- DDE active sharing : ddeshare
- Device Manager : devmgmt.msc
- DirectX Control Panel (if installed) : directx.cpl
- DirectX Diagnostic Utility : dxdiag
- Disk Cleanup : cleanmgr
- System Information=dxdiag
- Disk Defragmenter : dfrg.msc
- Disk Management : diskmgmt.msc
- Partition manager : diskpart
- Display Properties : control desktop
- Properties of the display (2) : desk.cpl
- Properties display (tab "appearance") : control color
- Dr. Watson: drwtsn32
- Manager vérirficateur drivers : check
- Event Viewer : Eventvwr.msc
- Verification of signatures of files: sigverif
- Findfast (if present) : findfast.cpl
- Folder Options : control folders
- Fonts (fonts) : control fonts
- Fonts folder windows : fonts
- Free Cell ...: freecell
- Game Controllers : Joy.cpl
- Group Policy (XP Pro) : gpedit.msc
- Hearts (card game) : mshearts
- IExpress (file generator. Cab) : IExpress
- Indexing Service (if not disabled) : ciadv.msc
- Internet Properties : inetcpl.cpl
- IPConfig (display configuration): ipconfig / all
- IPConfig (displays the contents of the DNS cache): ipconfig / displaydns
- IPConfig (erases the contents of the DNS cache): ipconfig / flushdns
- IPConfig (IP configuration cancels maps): ipconfig / release
- IPConfig (renew IP configuration maps) : ipconfig / renew
- Java Control Panel (if present) : jpicpl32.cpl
- Java Control Panel (if present) : javaws
- Keyboard Properties: control keyboard
- Local Security Settings : secpol.msc
- Local Users and Groups: lusrmgr.msc
- Logout: logoff
- Microsoft Chat : winchat
- Minesweeper (game): winmine
- Properties of the mouse: control mouse
- Properties of the mouse (2): main.cpl
- Network Connections : control NetConnect
- Network Connections (2): ncpa.cpl
- Network configuration wizard: netsetup.cpl
- Notepad : notepad
- NView Desktop Manager (if installed): nvtuicpl.cpl
- Manager links: packager
- Data Source Administrator ODBC: odbccp32.cpl
- Screen Keyboard: OSK
- AC3 Filter (if installed) : ac3filter.cpl
- Password manager (if present): Password.cpl
- Monitor performance : perfmon.msc
- Monitor performance (2): perfmon
- Dialing Properties (phone): telephon.cpl
- Power Options : powercfg.cpl
- Printers and Faxes : control printers
- Private Character Editor : eudcedit
- Quicktime (if installed) : QuickTime.cpl
- Regional and Language Options: intl.cpl
- Editor of the registry : regedit
- Remote desktop connection : mstsc
- Removable Storage: ntmsmgr.msc
- requests the operator to removable storage: ntmsoprq.msc
- RSoP (traduction. ..) (XP Pro): rsop.msc
- Scanners and Cameras : sticpl.cpl
- Scheduled Tasks : control schedtasks
- Security Center : wscui.cpl
- Console management services: services.msc
- shared folders : fsmgmt.msc
- Turn off windows : shutdown
- Sounds and Audio Devices : mmsys.cpl
- Spider (card game): spider
- Client Network Utility SQL server : cliconfg
- System Configuration Editor : sysedit
- System Configuration Utility : msconfig
- System File Checker (SFC =) (Scan Now) : sfc / scannow
- SFC (Scan next startup): sfc / scanonce
- SFC (Scan each démarraget) : sfc / scanboot
- SFC (back to default settings): sfc / revert
- SFC (purge cache files): sfc / purgecache
- SFC (define size CAHC x) : sfc / cachesize = x
- System Properties : sysdm.cpl
- Task Manager : taskmgr
- Telnet client : telnet
- User Accounts : nusrmgr.cpl
- Utility Manager (Magnifier, etc) : utilman
- Windows firewall (XP SP2) : firewall.cpl
- Microsoft Magnifier: magnify
- Windows Management Infrastructure: wmimgmt.msc
- Protection of the accounts database: syskey
- Windows update: wupdmgr
- Introducing Windows XP (if not erased) : tourstart
- Wordpad : write
- Date and Time Properties : timedate.cpl
Computer Programming Algorithms Directory
Welcome to my computer programming algorithms directory. I am hoping
to provide a comprehensive directory of web sites that detail
algorithms for computer programming problems. If you know of any web
sites that describe an algorithm (or multiple algorithms), please share here
Encryption Algorithms
- Advanced Encryption Standard (AES), Data Encryption Standard (DES), Triple-DES and Skipjack Algorithms - Offers descriptions of the named encryption algorithms.
- Blowfish - Describes the Blowfish encryption algorithm. Offers source code for a variety of platforms.
- KremlinEncrypt - Cryptography site provides an overview of cryptography algorithms and links to published descriptions where available.
- PowerBASIC Crypto Archives - Offers PowerBASIC source code for many algorithms including:
- Hashing - RIPEMD-160, MD5, SHA-1, SHA-256, CRC-16, CRC-32, Adler-32, FNV-32, ELF-32
- Encryption - RSA-64, Diffie-Hellman-Merkle Secure Key Exchange, Rijndael, Serpent, Twofish, CAST-128, CAST-256, Skipjack, TEA, RC4, PC1, GOST, Blowfish, Caesar Substitutional Shift, ROT13
- Encoding - Base64, MIME Base64, UUEncode, yEnc, Neuronal Network, URLEncode, URLDecode
- Compression - LZ78, LZSS, LZW, RLE, Huffman, Supertiny
- Psuedo-Random Number Generation (PRNG) - Mersenne Twister Number Generator, Cryptographic PRNG, MPRNG, MOAPRNG, L'Ecuyer LCG3 Composite PRNG, W32.SQL-Slammer
- xICE - Has links towards the bottom of the page to the description of the xice encryption algorithm as well as the xice software development kit which contains the algorithm's full source code in C++, ASP, JScript, Ruby, and Visual Basic 6.0.
Genetic Algorithms
- Artificial Life - Offers executable and source for ant food collection and the travelling salesman problems using genetic algorithms
- Genetic Ant Algorithm - Source code for a Java applet that implements the Genetic Ant Algorithm based upon the model given in Koza, Genetic Programming, MIT Press
- Introduction to Genetic Algorithms - Introduces fundamentals, offers Java applet examples
- Jaga - Offers a free, open source API for implementing genetic algorithms (GA) and genetic programming (GP) applications in Java
- SPHINcsX - Describes a methodology to perform a generalized zeroth-order two- and three-dimensional shape optimization utilizing a genetic algorithm
GIS (Geographic Information Systems) Algorithms
- Efficient Triangulation Algorithm Suitable for Terrain Modelling - Describes algorithm and includes links to source code for various languages
- Prediction of Error and Complexity in GIS Algorithms - Describes algorithms for GIS sensitivitiy analysis
- Point in Polygon Algorithm - Describes algorithm
Sorting Algorithms
- Andrew Kitchen's Sorting Algorithms - Describes parallel sorting algorithms:
- Odd-Even Transposition Sort has a worst case time of O(n), running on n processors. Its absolute speed up is O(log n), so its efficiency is O((log n)/n)
- Shear Sort has a worst case time of O(n½ log n), running on n processors. Its absolute speed up is O(n½), so its efficiency is O(1/n½)
- Ariel Faigon's Library of Sorting Algorithms - C source code for a variety of sorting algorithms including Insertion Sort, Quick Sort, Shell Sort, Gamasort, Heap Sort and Sedgesort (Robert Sedgewick quicksort optimization)
- Flash Sort - Describes the FlashSort algorithm which sorts n elements in O(n) time
- Michael Lamont's Sorting Algorithms - Describes common sorting algorithms:
- O(n²) Sorts - bubble, insertion, selection and shell sorts
- O(n log n) Sorts - heap, merge and quick sorts
- Sequential and Parallel Sorting Algorithms - Describes many sorting algorithms:
- Quicksort
- Heapsort
- Shellsort
- Mergesort
- Sorting Networks
- Bitonic Sort
- Odd-Even Mergesort
- LS3-Sort
- 4-way Mergesort
- Rotate Sort
- 3n-Sort
- s^2-way Mergesort
Search Algorithms
- Exact String Matching Algorithms - Details 35 exact string search algorithms.
- Finding a Loop in a Singly Linked List - Outlines several methods for identifying loops in a singly linked list.
- Fibonaccian search - Describes an O(log n) search algorithm for sorted arrays that is faster than a binary search for very large arrays.
Tree Algorithms
- B-Trees: Balanced Tree Data Structures - Introduction to B-Trees. Describes searching, splitting and inserting algorithms.
- MinHeap: C++ Template Implementation of Minimum Heap Algorithm
Computational Geometry Algorithms
- GeoLib - Downloadable Gnu GPL (free for non-commercial use) library of C++ computational geometry algorithms. Included in the library is a class representing a latitude and longitude position which provides conversion to Cartesian co-ordinates allowing Geospatial polygon representation.
- CGAL - Offers open source C++ library of computational geometry algorithms.
- FastGEO - Offers source code for a library of computational geometry algorithms such as geometrical primitives and predicates, hull construction, triangulation, clipping, rotations and projections using the Object Pascal language.
- Wykobi - FastGEO library ported to C++.
Phonetic Algorithms
- Lawrence Philips' Metaphone Algorithm - Describes an algorithm which returns the rough approximation of how an English word sounds. Offers a variety of source code listings for the algorithm.
- Soundex Algorithms - Describes the NYSIIS VS Soundex and R. C. Russell's soundex algorithms.
Project Management Algorithms
- Calculations for Critical Path Scheduling - Describes the algorithms for calculating critical paths with both ADM and PDM networks.
- Resource Leveling Using the Minimum Moment Heuristic - Offers a Windows 3.1 download that includes a .PDF document describing the algorithm.
- Project Scheduling Problem Solver - Heuristic based library for supporting research on the Resource Constrained Scheduling Problem. Provides an OOP API for the visualization, representation and solving of RCPSP.
- Resource-Constrained Project Scheduling - (.PDF) Describes several algorithms for resource leveling:
- Basic Single Mode RCPSP
- Basic Multi-Mode RCPSP
- Stochastic RCPSP
- Bin Packing related RCPSP
- Multi-resource constrained project scheduling problem (MRCPSP)
Miscellaneous Algorithms
- AI Horizon - Has a variety of algorithms, from basic computer science data structures such as 2-3 trees to AI-related algorithms such as minimax and a discussion of machine learning algorithms.
- CS Animated - Describes a variety of algorithms using narrated slideshow presentations (videos).
- Global Optimization Algorithms - Theory and Application - This is a free ebook (600+ page .PDF file) that focuses on evolutionary computation by discussing evolutionary algorithms, genetic algorithms, genetic programming, learning classifier systems, evolution strategy, differential evolution, particle swarm optimization, and ant colony optimization. It also elaborates on meta-heuristics like simulated annealing, hill climbing, tabu search, and random optimization. It contains many pseudocode descriptions for the algorithms.
- Hash Algorithms - Overview and source code (in C, Pascal and Java) for many general purpose hashing algorithms.
- Porter Stemming Algorithm - Describes a process for removing the commoner morphological and inflexional endings from words in English. Its main use is as part of a term normalisation process that is usually done when setting up Information Retrieval systems.
- Rubik's Cube - Solves a Rubic's Cube using the BestFast search algorithm and profile tables.
- Simulated Annealing - The fundamental idea is to allow moves resulting in solutions of worse quality than the current solution (uphill moves) in order to escape from local minima. The probability of doing such a move is decreased during the search.
- The Stony Brook Algorithm Repository
- Offers a collection of algorithm implementations for over seventy of
the most fundamental problems in combinatorial algorithms:
- Data Structures - Dictionaries, Priority Queues, Suffix Trees and Arrays, Graph Data Structures, Set Data Structures, Kd-Trees
- Numerical Problems - Solving Linear Equations, Bandwidth Reduction, Matrix Multiplication, Determinants and Permanents, Linear Programming/Simplex Method, Random Number Generation, Factoring and Primality Testing, Arbitrary Precision Arithmetic, Knapsack Problem, Discrete Fourier Transform
- Combinatorial Problems - Sorting, Searching, Median and Selection, Permutations, Subsets, Partitions, Graphs, Calendrical Calculations, Job Scheduling, Satisfiability
- Graph Problems - Polynomial Time Problems (Connected Components, Topological Sorting, Minimum Spanning Tree, Shortest Path, Transitive Closure and Reduction, Matching, Eulerian Cycle / Chinese Postman, Edge and Vertex Connectivity, Network Flow, Drawing Graphs Nicely, Drawing Trees, Planarity Detection and Embedding)
- Graph Problems - Hard Problems (Clique, Independent Set, Vertex Cover, Traveling Salesman Problem, Hamiltonian Cycle, Graph Partition, Vertex Coloring, Edge Coloring, Graph Isomorphism, Steiner Tree, Feedback Edge/Vertex Set
- Computational Geometry - Robust Geometric Primitives, Convex Hull, Triangulation, Voronoi Diagrams, Nearest Neighbor Search, Range Search, Point Location, Intersection Detection, Bin Packing, Medial-Axis Transformation, Polygon Partitioning, Simplifying Polygons, Shape Similarity, Motion Planning, Maintaining Line Arrangements, Minkowski Sum
- Set and String Problems - Set Cover, Set Packing, String Matching, Approximate String Matching, Text Compression, Cryptography, Finite State Machine Minimization, Longest Common Substring, Shortest Common Superstring
- EasyAlgorithm - Provides C source code for many basic algorithms covering data structures, containers, sorting and searching.
- Introduction to Neural Networks - Describes the Back Propagation algorithm for neural networks.
- NIST Dictionary of Algorithms and Data Structures - Some entries have links to implementations.
Other Stuff
- IT Support - Need help with your computer? These folks offer IT support services in the UK.
- Youtube to mp3 - Convert YouTube videos to mp3 files (free).
- Download Youtube - Another site to convert YouTube videos to mp3 files (free).
- SEO Services - Singapore based company offers guarantee for page 1 Google rankings.
- PM Bug - Discussion forum for precious metals enthusiasts.
Saturday, December 31, 2011
0 How Can You Make Buffer Overflow The System?
Buffer Overflow your system using batch file.
- Download text file from here.
- Save it as buffer.bat
- Now Open this batch file and you have done.
- With a little bit knowledge, you can make it more vulnerable.
How To Protect In Cafe/Public Computers While Surfing Internet?
People who surf internet on cafe/public computers, are more vulnerable to be hacked, reason is simple! They are unaware from the software installed on public computers, their privileges. It's always secure to access internet from your personal computers, but some times you have to access it from other places like cafe, your friend computer. So what if you wanna to secure yourself from these hacks? Two things you must keep in mind while surfing from pubic computers:
1. Always prefer to private browsing. Mostly people are unaware from this wonderful feature of browsers. So what is private browsing and how to enable it?
- Private Browsing allows you to browse the Internet without saving any information about which sites and pages you’ve visited, private browsing do not save Visited pages, History, Passwords, Cookies and Cache files.
- For enabling it, press Ctrl+Shift+P for firefox and IE users (For chrome use shortcut Ctrl+Shift+N , a prompting window will ask you for starting private browsing.
2. Use On-Screen Keyboard. What to do if you think there is suspicious keylogger installed on system. Don't take risk, use on-screen keyboard. Keyloggers captures information from normal keyboard only. So whenever you do login on your personal internet banking accounts or else, always prefer to use virtual keyboard. You can open it by typing OSK in run.
How To Remotely Log Out Facebook From All Other Computer/Devices?
Sometimes users do login from any unfamiliar computer/cyber cafe & forget to log out or any computer failure occurs. You must not bother about it as you can log out from all other computers without using that computer again. Follow these steps:
- Login to your facebook.
- Go to Account> Account Setting> Under Setting tab> Account Security. There you will see something as shown below only if your facebook account is opened from other location otherwise you will see only recent login information.
- Click on end activity will log out from all other computers.
Friday, December 30, 2011
Add More Security To Your Google Account Using 2-Step Verification
Hi friends!! Today I'm telling about how you can add more security to your Google account using 2-step verification. 2-step verification is the best way for securing your Google account even if your password is stolen. You can't login to your account unless you have the verification code. Using it, you have to required both password & verification code (Receive on your mobile via SMS) for accessing your Gmail, Orkut services. You must be aware about security provided by Google.
- Login to your Google account.
- Open this link https://www.google.com/accounts/SmsAuthConfig
- Click on Start setup.
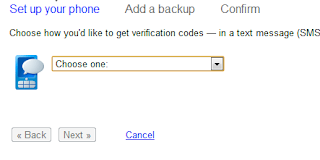
- Now Set up your phone: Choose appropriate option (me chose Text message (SMS) or voice call under Landline or mobile phone).
- Choose your country & Enter your mobile number.
- Choose the option Send codes by: SMS text message or Voice call (I prefer to SMS text message).
- Click on Send code under Let's the test phone.
- You will receive a code via text if you chose SMS text message.
- Enter code in next field & click on Verify.
- Click on Next.
Your phone is now configured to receive verification codes. Now make backup in the case if you lost your phone or is unavailable.
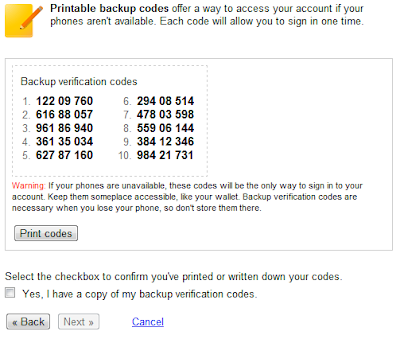
- Click on Next.
- Print Backup verification codes or save it.
Remember: Each backup verification code can be use only once for verification & keep these codes secret. Read the warning under backup verification codes carefully. - Check Yes, I have a copy of my backup verification codes & click on Next.
- Now add another phone number that belongs to you or a trusted friend or family member.
- Follow the steps as described above for sending code & optional testing.
- Click on Next.
- Click on Turn on 2-step verification
- That's all.
When you will sign in to your Google account using user id & password, it will ask for verification code send to your phone. You must require verification code for accessing your account.
If you didn't receive code, then you can use another ways for getting verification code as shown below.
Subscribe to:
Comments (Atom)